Remote IoT On Mac: Connect Behind Firewall, No Windows Needed
Connecting to your Internet of Things (IoT) devices remotely, especially when they are tucked away behind a firewall on your Mac, can often feel like deciphering a complex puzzle. Many users find themselves restricted when trying to access their IoT ecosystem from a macOS environment, assuming a Windows machine is the only way out. However, the good news is, accessing remote IoT behind a router on a Mac without relying on Windows is entirely possible with the right tools and techniques. This comprehensive guide aims to provide you with practical insights and actionable steps to achieve a secure remote connection for IoT devices behind a firewall using your Mac.
With the increasing reliance on IoT technology for everything from smart homes to industrial automation, understanding how to bypass firewall restrictions while maintaining robust security has become essential. This article will explore various methods and tools to remotely connect IoT devices behind a firewall on a Mac, ensuring that your network remains protected. We’ll show you how to set up a secure and efficient remote connection on your Mac without compromising your network’s security, proving that you don't need to download Windows or any other OS. If you’re here, chances are you’ve faced this very challenge, and we're here to provide the solutions.
Table of Contents
- Understanding the Challenge: IoT, Firewalls, and macOS
- Core Strategies for Remote IoT Connectivity on Mac
- Method 1: SSH (Secure Shell) – Your Command-Line Gateway
- Method 2: VPN (Virtual Private Network) – Creating a Secure Tunnel
- Method 3: Reverse SSH Tunneling – Bypassing Strict Firewalls
- Method 4: Cloud-Based IoT Platforms with Mac Integration
- Essential Tools for Mac Users: Beyond the Basics
- Maintaining Security and Troubleshooting Common Issues
Understanding the Challenge: IoT, Firewalls, and macOS
Connecting IoT devices remotely behind a firewall on your Mac can feel like solving a puzzle blindfolded. The primary hurdle is the firewall itself, designed to protect your network from unauthorized access. While this protection is crucial, it also inherently blocks incoming connections that you might want for your IoT devices. So, what are the most effective strategies to remotely connect to your IoT devices behind a firewall on a Mac? The options are diverse, each with its own strengths and considerations, ensuring you don't need to resort to Windows.
What Exactly is a Firewall and Why Does it Matter for IoT?
At its core, a firewall is a network security system that monitors and controls incoming and outgoing network traffic based on predetermined security rules. Think of it as a digital gatekeeper for your network. For IoT devices, which are often small, resource-constrained, and sometimes have less robust security features than traditional computers, firewalls are vital. They prevent malicious actors from scanning for open ports, exploiting vulnerabilities, or gaining unauthorized access to your devices and, by extension, your entire network. Most home and business networks have a router that acts as a firewall, implementing Network Address Translation (NAT) and blocking unsolicited incoming connections by default.
The challenge arises when you, as a legitimate user, want to access your IoT device from outside your local network. Since the firewall blocks incoming connections, your remote access requests are typically denied. This is why a direct connection is often impossible without specific configurations. Understanding this fundamental barrier is the first step toward devising a successful remote connection strategy for your IoT devices on your Mac.
The macOS Advantage (and Perceived Limitations)
macOS is renowned for its robust Unix-based foundation, which provides powerful command-line tools and native support for many networking protocols. This makes it an excellent platform for managing and connecting to IoT devices. However, many users perceive a limitation when trying to access their IoT ecosystem from a macOS environment, often assuming that specialized Windows software or complicated workarounds are necessary. This perception is largely unfounded. macOS, with its built-in utilities and a thriving ecosystem of open-source tools, is perfectly capable of handling complex remote connectivity scenarios without needing to download Windows or run virtual machines.
The perceived difficulty often stems from unfamiliarity with command-line interfaces or the specific networking concepts involved, rather than an actual technical limitation of macOS. In fact, for Mac users, tools like Tunnelblick, OpenSSH, and Mosquitto provide reliable solutions for establishing secure connections to IoT devices behind firewalls. This guide will leverage these native macOS capabilities to show you how to establish secure and efficient remote connections, proving that your Mac is more than capable of managing your IoT needs.
Core Strategies for Remote IoT Connectivity on Mac
Connecting to an IoT device remotely while it's behind a firewall on a Mac can seem daunting, but with the right approach, it's entirely achievable. The options are diverse, each with its own strengths and ideal use cases. This article will guide you through the process of remote connecting IoT devices behind a firewall on a Mac without downloading additional software beyond what's freely available and standard for macOS. We'll cover various methods and tools, ensuring you can pick the best strategy for your specific needs. The key is to understand how to create a secure tunnel or a pathway through or around the firewall without compromising your network's integrity. These strategies are all Mac-native, ensuring you won't need to touch a Windows machine.
The most common and effective strategies involve leveraging secure communication protocols and network configurations. These include:
- **SSH (Secure Shell):** A fundamental protocol for secure remote access and tunneling.
- **VPN (Virtual Private Network):** Creating a secure, encrypted tunnel to your home or office network.
- **Reverse SSH Tunneling:** A clever technique where the IoT device initiates the connection outwards.
- **Cloud-Based IoT Platforms:** Utilizing third-party services that abstract away network complexities.
Method 1: SSH (Secure Shell) – Your Command-Line Gateway
SSH (Secure Shell) is an essential protocol for securely connecting to remote devices, including IoT (Internet of Things) devices. It provides an encrypted connection over an unsecured network, making it ideal for managing devices that might be in a different physical location or behind a firewall. For Mac users, SSH is built right into macOS, meaning you don't need to download any extra software to get started. This method provides a robust solution, allowing you to establish a secure connection and bypass firewall restrictions for your remote IoT on Mac.
One of the challenges of using remote IoT behind a firewall with SSH is that direct incoming connections are typically blocked. This is where port forwarding comes into play. Port forwarding, configured on your router, tells the router to send specific incoming traffic on a designated port to a particular device on your local network. For example, you might forward port 22 (the standard SSH port) from your router's public IP address to the private IP address of your IoT device. However, this requires access to your router's settings and a static public IP address or a Dynamic DNS (DDNS) service if your public IP changes frequently. This is a common and effective way to allow your Mac to connect directly to the IoT device's SSH server.
Setting Up SSH for IoT Remote Access
To set up SSH for remote IoT access on your Mac, follow these steps:
- **Enable SSH on your IoT Device:** Most Linux-based IoT devices (like Raspberry Pi) have SSH capabilities. Ensure SSH is enabled. For example, on a Raspberry Pi, you can enable it via `raspi-config`.
- **Find Your IoT Device's Local IP Address:** Use network scanning tools (like `nmap` or your router's admin page) to find the local IP address of your IoT device.
- **Configure Port Forwarding on Your Router:**
- Log in to your router's administration page (usually via a web browser, e.g., `192.168.1.1`).
- Navigate to the "Port Forwarding" or "NAT" section.
- Create a new rule:
- **External Port:** Choose a high, non-standard port (e.g., 2222, 50000) for security.
- **Internal Port:** 22 (the standard SSH port).
- **Internal IP Address:** The local IP address of your IoT device.
- **Protocol:** TCP.
- Save the settings.
- **Determine Your Public IP Address:** You can find this by searching "what is my IP" on Google or using a service like `ipinfo.io`. If your IP changes, consider a DDNS service (e.g., No-IP, DuckDNS).
- **Connect from Your Mac:** Open Terminal on your Mac and use the `ssh` command:
For example: `ssh -p 2222 pi@myiotdevice.ddns.net`ssh -p [External_Port] [username]@[Your_Public_IP_or_DDNS_Hostname] - **Use SSH Keys for Enhanced Security:** Instead of passwords, generate an SSH key pair on your Mac (`ssh-keygen`) and copy the public key to your IoT device (`ssh-copy-id`). This significantly enhances security and convenience.
This method allows your Mac to establish a direct, secure connection to your IoT device, effectively bypassing the firewall by explicitly telling the router to allow that specific incoming connection. It's a fundamental technique for remote connect IoT behind firewall mac download without Windows requirements.
Method 2: VPN (Virtual Private Network) – Creating a Secure Tunnel
Another highly effective and secure strategy for remote connecting IoT devices behind a firewall on your Mac is by using a Virtual Private Network (VPN). A VPN creates an encrypted tunnel between your Mac and your home or office network where your IoT devices reside. Once connected to the VPN, your Mac effectively becomes part of that local network, allowing you to access all devices on it as if you were physically present. This method is particularly powerful because it doesn't require individual port forwarding for each IoT device; once the VPN connection is established, all local network resources become accessible.
The options for setting up a VPN are diverse. You can use a dedicated VPN server running on your home router (many modern routers support this), a dedicated VPN appliance, or even an IoT device itself (like a Raspberry Pi) configured as a VPN server. For Mac users, integrating with these VPN solutions is straightforward. Tools like Tunnelblick (an OpenVPN client for macOS) make connecting to OpenVPN servers incredibly easy, eliminating any need for Windows-specific software or configurations. This approach offers a holistic solution for your remote IoT on Mac needs, securing not just one device but your entire local network access.
Configuring a VPN on Your Mac for IoT Access
Setting up a VPN for remote IoT access involves two main parts: configuring the VPN server on your home network and configuring your Mac to connect to it.
**Part 1: Setting up the VPN Server (Example: OpenVPN on Router/Raspberry Pi)**
- **Check Router VPN Capabilities:** Many high-end routers (e.g., Asus, Netgear, TP-Link with custom firmware like DD-WRT or OpenWrt) have built-in OpenVPN server functionality. Consult your router's manual.
- **Dedicated VPN Server (e.g., Raspberry Pi):** If your router doesn't support VPN, you can set up a dedicated VPN server on an IoT device like a Raspberry Pi using software like OpenVPN or WireGuard. Projects like PiVPN simplify this process significantly.
- Install OpenVPN/WireGuard on your chosen server device.
- Generate client configuration files. These files (often `.ovpn` for OpenVPN) contain all the necessary information for your Mac to connect.
- Ensure the VPN server's port (e.g., UDP 1194 for OpenVPN) is forwarded on your main router to the VPN server's local IP address.
- Set up a DDNS service if your public IP address is dynamic.
**Part 2: Connecting from Your Mac**
- **Download a VPN Client:** For OpenVPN, the most popular and user-friendly client for macOS is Tunnelblick. Download and install it. For WireGuard, you can use the official WireGuard app from the Mac App Store.
- **Import the VPN Configuration:**
- **For Tunnelblick:** Double-click the `.ovpn` configuration file you generated from your VPN server. Tunnelblick will prompt you to install it.
- **For WireGuard:** Open the WireGuard app, click the "+" icon, and select "Import tunnel(s) from file" or "Add Empty Tunnel" and paste the configuration.
- **Connect to the VPN:**
- **For Tunnelblick:** Click the Tunnelblick icon in your menu bar and select "Connect [Your VPN Name]".
- **For WireGuard:** Click "Activate" next to your tunnel name in the app.
- **Access Your IoT Devices:** Once connected, your Mac will have an IP address within your home network's subnet. You can then access your IoT devices using their local IP addresses as if you were physically at home. For example, if your IoT device is at `192.168.1.100`, you can simply `ssh 192.168.1.100` from your Mac's Terminal.
This method provides a highly secure and flexible way to remotely connect IoT devices behind a firewall on your Mac, without any reliance on Windows. It centralizes your remote access through a single secure tunnel, simplifying management.
Method 3: Reverse SSH Tunneling – Bypassing Strict Firewalls
When direct incoming connections are strictly blocked by a firewall, or when you don't have control over the router's port forwarding settings, reverse SSH tunneling emerges as an ingenious solution. This method flips the traditional connection on its head: instead of your Mac initiating a connection to the IoT device, the IoT device initiates an outbound connection to a publicly accessible server (often a cheap VPS or a dedicated server you control). Your Mac then connects to that public server, and through the established reverse tunnel, gains access to the IoT device. This is particularly useful for remote connect IoT behind firewall mac download scenarios where the device is in a highly restricted network environment.
The beauty of reverse SSH tunneling is that it leverages the fact that most firewalls allow outbound connections. The IoT device "calls home" to your public server, creating a persistent, secure tunnel. Your Mac then simply connects to a specific port on that public server, and the traffic is securely forwarded through the tunnel to your IoT device. This method requires a third-party server with a public IP address, but it completely bypasses the need for port forwarding on the IoT device's local network, making it incredibly versatile for remote IoT on Mac.
Here’s how to set it up:
- **A Publicly Accessible Server (Jump Server):** You'll need a server with a static public IP address that you can SSH into. A small Virtual Private Server (VPS) from providers like DigitalOcean, Linode, or Vultr is perfect for this. Let's call this `your_public_server.com`.
- **Configure the IoT Device to Initiate the Reverse Tunnel:** On your IoT device (e.g., Raspberry Pi), you'll run an SSH command that creates the reverse tunnel. This command tells the IoT device to connect to your public server and open a specific port on that server that will forward traffic back to the IoT device's local SSH port (22).
For example: `ssh -N -R 8080:localhost:22 user@your_public_server.com`ssh -N -R [Public_Server_Port]:localhost:22 [username]@[your_public_server.com]- `-N`: Do not execute a remote command.
- `-R`: Specifies a remote port forwarding. `[Public_Server_Port]` is the port on `your_public_server.com` that will be forwarded. `localhost:22` refers to the IoT device's local SSH port.
- It's highly recommended to use SSH keys for authentication to avoid password prompts and enable automated connections.
- You might want to use a tool like `autossh` on the IoT device to keep the tunnel persistent in case of network drops.
- **Configure the Public Server to Allow GatewayPorts:** On `your_public_server.com`, you might need to enable `GatewayPorts` in the SSH daemon configuration (`/etc/ssh/sshd_config`) to allow other clients (your Mac) to connect to the forwarded port. Set `GatewayPorts yes` and restart the SSH service (`sudo systemctl restart sshd`).
- **Connect from Your Mac:** Now, from your Mac, you can SSH into your IoT device by connecting to the specified port on your public server:
No, wait, this is incorrect. You connect to the public server, but specify the forwarded port on the public server.ssh -p [Public_Server_Port] [IoT_username]@localhost
For example: `ssh -p 8080 pi@your_public_server.com` When you connect to `your_public_server.com` on port `8080`, the traffic is then relayed through the reverse tunnel to the `pi` user on the IoT device's local SSH port (22).ssh -p [Public_Server_Port] [IoT_username]@[your_public_server.com]
This method effectively "punches a hole" through the firewall from the inside out, providing a secure and reliable way to remote connect IoT behind firewall on your Mac, entirely independent of Windows-specific solutions.
Method 4: Cloud-Based IoT Platforms with Mac Integration
For those seeking a simpler, more scalable approach to remote connect IoT behind firewall on a Mac, leveraging cloud-based IoT platforms is an excellent option. Services like AWS IoT Core, Google Cloud IoT Core, and Microsoft Azure IoT Hub are designed to manage vast numbers of IoT devices, abstracting away the complexities of network connectivity, security, and data ingestion. While they involve a third-party service, they often provide SDKs and tools that integrate seamlessly with macOS, negating the need for Windows environments or complex manual network configurations.
These platforms work by having your IoT devices connect outbound to the cloud service. Since outbound connections are typically allowed by firewalls, the devices can establish a persistent, secure connection to the cloud. Your Mac then interacts with the cloud platform's API or dashboard to send commands to and receive data from your IoT devices. This method is particularly attractive for large deployments or when you need robust security features, device management capabilities, and data analytics without delving deep into network engineering. As businesses and individuals increasingly rely on IoT devices, understanding how to configure them securely via cloud platforms is essential.
Here’s a general overview of how this works with your Mac:
- **Register Your IoT Devices with the Cloud Platform:** Each IoT device is registered with the chosen cloud platform. This typically involves assigning a unique ID and provisioning security credentials (e.g., X.509 certificates or shared keys).
- **Install Platform SDK/Libraries on IoT Devices:** Your IoT devices will run client software (provided by the cloud platform, often in Python, C++, Node.js, etc.) that connects to the cloud. This client handles secure communication, message queuing, and device shadows.
- **IoT Devices Connect Outbound:** The IoT devices initiate connections to the cloud platform's endpoints (e.g., MQTT broker, HTTP API). These are outbound connections, so they usually pass through firewalls without issue.
- **Manage from Your Mac:**
- **Web Console:** Most cloud platforms offer comprehensive web-based management consoles. You can access these from any web browser on your Mac to monitor device status, send commands, and view data.
- **CLI Tools:** AWS, Google Cloud, and Azure all provide powerful command-line interface (CLI) tools that are fully compatible with macOS. You can install these on your Mac and use them to programmatically interact with your IoT devices through the cloud platform. For example, with AWS CLI, you can publish MQTT messages to a topic your device subscribes to.
- **SDKs/APIs:** If you're developing custom applications on your Mac, you can use the platform's SDKs (available for various programming languages) to build applications that communicate with your IoT devices via the cloud.
This approach simplifies the networking aspect significantly, as the cloud platform handles the firewall traversal. It allows you to focus on the IoT application logic and data, making it a powerful solution for remote connect IoT behind firewall mac download scenarios, without the need for intricate network configurations or Windows-specific tools.
Essential Tools for Mac Users: Beyond the Basics
While macOS provides robust built-in capabilities for networking and security, several external tools and protocols significantly enhance your ability to remotely connect IoT devices behind a firewall on your Mac. These tools are either native to macOS, widely available as open-source projects, or designed with cross-platform compatibility in mind, ensuring a seamless experience without relying on Windows. For Mac users, tools like Tunnelblick, OpenSSH, and Mosquitto provide reliable solutions for establishing secure connections to IoT devices behind firewalls, proving that the macOS ecosystem is well-equipped for this task.
Here are some essential tools and concepts that every Mac user dealing with remote IoT should be familiar with:
- **OpenSSH (Built-in):**
As discussed, OpenSSH is the backbone of secure remote access. It's pre-installed on macOS, meaning you can open Terminal and immediately start using `ssh`, `scp` (for secure file copying), and `sftp` (for secure file transfer). Mastering SSH key generation (`ssh-keygen`) and management (`ssh-agent`, `ssh-add`) is crucial for both security and convenience. This is your primary tool for command-line access to your remote IoT on Mac devices.
- **Tunnelblick (OpenVPN Client):**
If you choose the VPN route, Tunnelblick is the go-to OpenVPN client for macOS. It's a free, open-source graphical user interface for OpenVPN, making it incredibly easy to import and manage VPN configurations. It seamlessly integrates with the macOS menu bar, allowing you to connect and disconnect with a single click. It's a prime example of how Mac users can achieve complex network configurations without proprietary software or Windows.
- **Mosquitto (MQTT Broker/Client):**
MQTT (Message Queuing Telemetry Transport) is a lightweight messaging protocol commonly used for IoT devices due to its efficiency and low bandwidth requirements. Mosquitto is an open-source MQTT broker (server) and client library. While you'd typically run the broker on a server (or your IoT device if it's powerful enough), you can install Mosquitto clients on your Mac (`brew install mosquitto`) to publish and subscribe to MQTT topics. This allows your Mac to directly communicate with your IoT devices via MQTT, often over an SSH tunnel or VPN, for real-time data exchange and command sending.
- **Homebrew (Package Manager):**
Homebrew is an
Remotely Connect to IoT via VNC : A Step-by-Step Guide
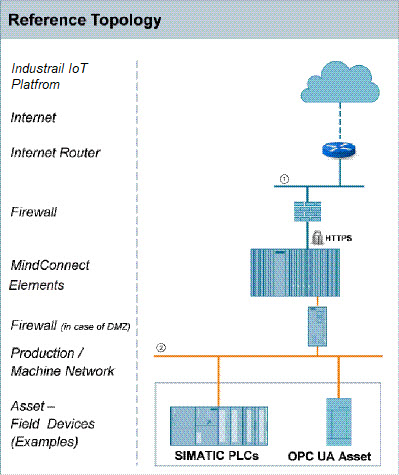
Firewall Settings - Developer Documentation

Remote Connect IoT: Unlocking The Power